Three common hacking tactics and how to defeat them
Published 25-OCT-2018 17:37 P.M.
|
4 minute read
Hey! Looks like you have stumbled on the section of our website where we have archived articles from our old business model.
In 2019 the original founding team returned to run Next Investors, we changed our business model to only write about stocks we carefully research and are invested in for the long term.
The below articles were written under our previous business model. We have kept these articles online here for your reference.
Our new mission is to build a high performing ASX micro cap investment portfolio and share our research, analysis and investment strategy with our readers.
Click Here to View Latest Articles
As we have come to know all too well, leaked documents and files can have a devastating effect on companies.
Look no further than British Airways and Cathay Pacific. The two airlines are now on the hook for considerable payouts to customers whose credit card details may well already have been sold.
As of August 29 this year, some 215 million records had been leaked or exposed via cyberattacks in 2018.
215 million.
When the number is that high, there’s a good chance that those in charge of security aren’t on top of their game as much as they should be. So if major companies are struggling, what about mid-sized business?
If you are running a business of any size, below are three common forms of cyberattack that companies are likely to face, and what can be done about them:
PHISHING:
Phishing is an old tactic, but the methodology behind phishing is becoming increasingly sophisticated.
Phishing costs mid-size companies US$1.6 million on average, with phishing attacks up 65% over the last 12 months.
Hackers will often wait for opportune moments to launch phishing attempts (such as security breaches in similar companies etc.) in an attempt to weed out those that wouldn’t fall for it normally.
A hacker will use phishing to pose as a legitimate third party or administrator, duplicating a copy of the email or website, prompting users to perform a password ‘reset’. Once the user clicks the email, they will be taken through to a site that looks like the real thing.
Upon entering their ‘old’ password, the hacker gains access to the user’s current password, compromising the entire system.
Tip: If you receive a password reset email, flag it with your system administrator or IT support team immediately and inform co-workers.
RANSOMWARE:
Simple rule: if you receive an email with an attachment from someone you don’t know: don’t open it.
It is age-old advice, but it couldn’t be more relevant today. Ransomware attacks have become a go-to move for hackers – surging a ludicrous 2,502% in 2017 alone. Yes, you read that figure correctly.
Ransomware is as egregious as the name suggests: a hacker will deploy a malicious file onto your server and utilise phishing (producing fraudulent emails from a reputable source) to send an email to everyone on the server.
If a user clicks through on the attachment, the ransomware file is deployed, encrypting highly sensitive files on the user’s computer or servers. The only way to unlock them again is to pay a specified amount to the hacker (which is usually through an untraceable medium like bitcoin).
Tip: If you don’t know who the email is from and the URL link looks odd – BIN IT
CRACKING:
If you get lackadaisical with your passwords then listen up.
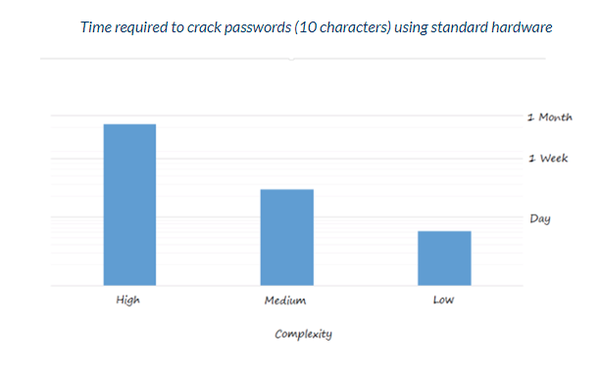
One of the most common forms of attack is through cracking, where a hacker will run a program that generates and authenticates billions of variations of simple passwords.
I’m as guilty of this as anyone: we still use laughably simple passwords, even for important log-ins.
* yolo
* Iamthebest
* Person’s DOB
* 111222
* favourite sport team
This trend is disturbing because we then love to re-use these passwords, which means if a hacker cracks one of your passwords on one account or device, you could be completely compromised.
You’d think the threat of this would be enough to encourage users to put more thought into stronger passwords, but we simply aren’t learning.
According to a recent study by preempt, an astonishing 35% of users have a ‘weak password’, while another 65% of passwords can be cracked if given enough time.
To counteract this, the study makes the following recommendations:
Use a password policy to enforce complexity and password expiration. (Note: Preempt can help force a password change when there is an indication that a password was compromised or is considered weak.)
1.Require longer passwords (8 bad, 10 ok, 12 good)
2.Educate people to:
1.Not share passwords with other employees
2.Not share passwords with other cloud services
3.Not use simple patterns, personal data or common words (make it unpredictable)
4.Not repeat passwords when a password expires (enumeration included)
3.Add additional factors to authenticate users. For example, on suspicious logins, you could send end users a simple email notification or push an immediate notification to their mobile device. (Preempt can help in such cases.)
4.Implement a context based solution - train and enforce password policy based on users activity (1b, 4).
These are just three attacks to be mindful of. There are plenty others. However if companies are vigilant and on top of trends, they can go a long way to protecting themselves and their customers’ sensitive information.
General Information Only
S3 Consortium Pty Ltd (S3, ‘we’, ‘us’, ‘our’) (CAR No. 433913) is a corporate authorised representative of LeMessurier Securities Pty Ltd (AFSL No. 296877). The information contained in this article is general information and is for informational purposes only. Any advice is general advice only. Any advice contained in this article does not constitute personal advice and S3 has not taken into consideration your personal objectives, financial situation or needs. Please seek your own independent professional advice before making any financial investment decision. Those persons acting upon information contained in this article do so entirely at their own risk.
Conflicts of Interest Notice
S3 and its associated entities may hold investments in companies featured in its articles, including through being paid in the securities of the companies we provide commentary on. We disclose the securities held in relation to a particular company that we provide commentary on. Refer to our Disclosure Policy for information on our self-imposed trading blackouts, hold conditions and de-risking (sell conditions) which seek to mitigate against any potential conflicts of interest.
Publication Notice and Disclaimer
The information contained in this article is current as at the publication date. At the time of publishing, the information contained in this article is based on sources which are available in the public domain that we consider to be reliable, and our own analysis of those sources. The views of the author may not reflect the views of the AFSL holder. Any decision by you to purchase securities in the companies featured in this article should be done so after you have sought your own independent professional advice regarding this information and made your own inquiries as to the validity of any information in this article.
Any forward-looking statements contained in this article are not guarantees or predictions of future performance, and involve known and unknown risks, uncertainties and other factors, many of which are beyond our control, and which may cause actual results or performance of companies featured to differ materially from those expressed in the statements contained in this article. S3 cannot and does not give any assurance that the results or performance expressed or implied by any forward-looking statements contained in this article will actually occur and readers are cautioned not to put undue reliance on forward-looking statements.
This article may include references to our past investing performance. Past performance is not a reliable indicator of our future investing performance.
