Cyber security report shares dire warnings
Published 19-FEB-2016 13:02 P.M.
|
4 minute read
Hey! Looks like you have stumbled on the section of our website where we have archived articles from our old business model.
In 2019 the original founding team returned to run Next Investors, we changed our business model to only write about stocks we carefully research and are invested in for the long term.
The below articles were written under our previous business model. We have kept these articles online here for your reference.
Our new mission is to build a high performing ASX micro cap investment portfolio and share our research, analysis and investment strategy with our readers.
Click Here to View Latest Articles
More than 30% of all applications used on laptops, mobiles and tablets have a critical vulnerabilities, that can be easily compromised for sensitive data, according to a cyber security report published by Hewlett Packard Enterprise (NYSE:HPE). HPE is a multinational technology company worth around US$25 billion, providing a wide range of IT solutions for corporate clients around the globe.
HPE’s annual Cyber Risk Report is designed to provide a better understanding of the threat landscape which all businesses now face and help them to minimise security risks in their operations.
Keen to address these challenges, start-up cyber security companies have hastily come to the fore considering the huge gap between what companies expect in terms of security and what they’re actually getting.
This year’s report focuses on the widening range of threats including open-source, mobile and the Internet of Things (IoT), noting that cyber-attacks are growing in frequency and severity.
According to HPE, “data compromise is no longer just about getting payment card information. It’s about getting information capable of changing someone’s life forever”.
“In 2015, we saw attackers infiltrate networks at an alarming rate, leading to some of the largest data breaches to date, but now is not the time to take the foot off the gas and put the enterprise on lockdown,” said Sue Barsamian, Senior Vice President and General Manager at HPE. “We must learn from these incidents, understand and monitor the risk environment, and build security into the fabric of the organisation to better mitigate known and unknown threats, which will enable companies to fearlessly innovate and accelerate business growth.”
The fastest growing cyber security battlefield is Mobiles
Web applications continue to cause problems for companies although its mobile connectivity that is attracting the most focus from hackers. HPE’s research shows that approximately 75% of all mobile applications scanned exhibited “at least one critical or high-severity security vulnerability, compared to 35% of non-mobile applications”.
In 2015, Microsoft Windows represented the most targeted software platform, with 42% of the top 20 exploits directed at Microsoft platforms and applications.
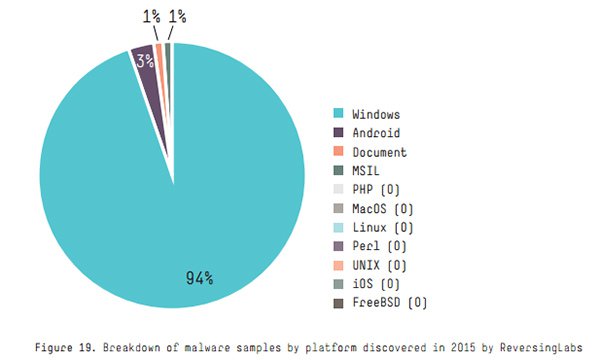
When it comes to malware, Windows is far and away the most popular target for hackers, recording 94% of all threats discovered as part of HPE’s research.
Malware has “evolved from being simply disruptive to a revenue-generating activity for attackers”. Although the overall number of newly discovered malware samples declined 3.6% year-over-year, the attack targets shifted notably and “focused heavily on monetisation”.
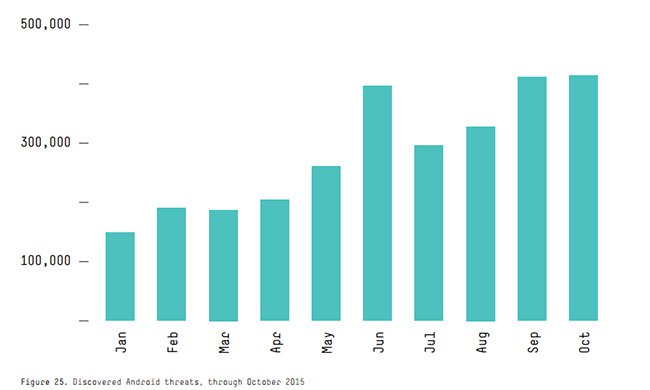
As the number of connected mobile devices expands, malware is diversifying to target the most popular mobile operating platforms such as Android and iOS. The number of Android threats, malware, and potentially unwanted applications have grown to more than 10,000 new threats discovered daily, reaching a total year-over-year increase of 153%. Over the course of 2015 HPE estimates that the Android platform saw a month-on-month increase between 100,000 threats in January 2015 to just under 400,000 by October.
Despite the sharp climb in Android vulnerabilities, the Apple iOS platform saw the greatest growth rate, increasing by 230%.
In another shocking finding, HPE detected that fraudsters are now able to bypass physical attacks on automatic teller machines (ATMs) and go directly into compromising the underlying software.
“In some cases, attacks at the software level bypass card authentication to directly dispense cash,” says HPE.
From point of sale to point of steal
As part of its findings HPE’s report criticises the lack of action among businesses as being part of the underlying problem.
The report found that the industry didn’t learn anything about patching in 2015. The number one most exploited vulnerability in 2015, was the most exploited in 2014, and has been patched by the vendor...twice”.
Going further and firing a shot across the bows of legislators and policymakers, HPE says that “many lawmakers in the US, UK and elsewhere claimed that security was only possible if fundamental rights of privacy and due process were abridged.”
In other words, for cyber security to improve civil liberties must be curtailed.
A far cry indeed, evoking Benjamin Franklin’s heeded warning: “They who can give up essential liberty to obtain a little temporary safety deserve neither liberty nor safety.”
For a full copy of the HPE Cyber Security Report 2016, click here.
General Information Only
S3 Consortium Pty Ltd (S3, ‘we’, ‘us’, ‘our’) (CAR No. 433913) is a corporate authorised representative of LeMessurier Securities Pty Ltd (AFSL No. 296877). The information contained in this article is general information and is for informational purposes only. Any advice is general advice only. Any advice contained in this article does not constitute personal advice and S3 has not taken into consideration your personal objectives, financial situation or needs. Please seek your own independent professional advice before making any financial investment decision. Those persons acting upon information contained in this article do so entirely at their own risk.
Conflicts of Interest Notice
S3 and its associated entities may hold investments in companies featured in its articles, including through being paid in the securities of the companies we provide commentary on. We disclose the securities held in relation to a particular company that we provide commentary on. Refer to our Disclosure Policy for information on our self-imposed trading blackouts, hold conditions and de-risking (sell conditions) which seek to mitigate against any potential conflicts of interest.
Publication Notice and Disclaimer
The information contained in this article is current as at the publication date. At the time of publishing, the information contained in this article is based on sources which are available in the public domain that we consider to be reliable, and our own analysis of those sources. The views of the author may not reflect the views of the AFSL holder. Any decision by you to purchase securities in the companies featured in this article should be done so after you have sought your own independent professional advice regarding this information and made your own inquiries as to the validity of any information in this article.
Any forward-looking statements contained in this article are not guarantees or predictions of future performance, and involve known and unknown risks, uncertainties and other factors, many of which are beyond our control, and which may cause actual results or performance of companies featured to differ materially from those expressed in the statements contained in this article. S3 cannot and does not give any assurance that the results or performance expressed or implied by any forward-looking statements contained in this article will actually occur and readers are cautioned not to put undue reliance on forward-looking statements.
This article may include references to our past investing performance. Past performance is not a reliable indicator of our future investing performance.
